Introduction to VPN Protocols
In the current digital landscape, safeguarding privacy and security is a top priority for internet users. As cyber threats and data breaches continue to escalate, the demand for secure communication methods is more pressing than ever. Virtual Private Networks (VPNs) offer a solution by using encryption and tunneling technologies to establish a secure link between users and the web, ensuring their data remains shielded from unauthorized access.
OpenVPN Protocol
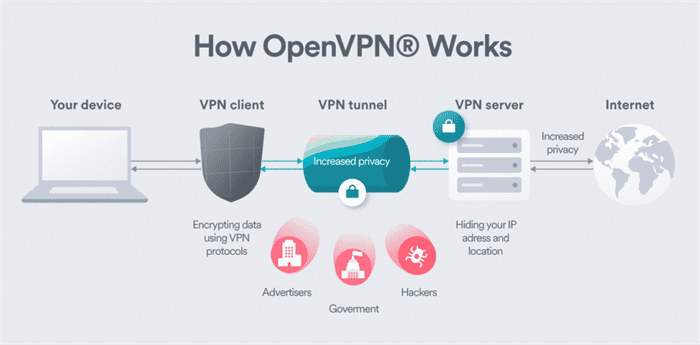
OpenVPN is widely regarded as one of the leading VPN protocols, largely because of its open-source framework and strong security measures. By utilizing SSL/TLS protocols for encryption, it provides robust protection against a wide range of cyber threats. OpenVPN is also highly versatile, with broad compatibility across numerous platforms and devices. Its combination of speed and reliability makes it particularly well-suited for activities like streaming and torrenting.
L2TP/IPsec Protocol

Layer 2 Tunneling Protocol (L2TP) paired with Internet Protocol Security (IPsec) is another commonly used VPN protocol. This combination delivers strong encryption and authentication, safeguarding the confidentiality and integrity of data during transmission. Although L2TP/IPsec offers solid security, it is generally slower than other protocols and can sometimes face compatibility challenges with specific networks and devices.
IKEv2 Protocol

Internet Key Exchange version 2 (IKEv2) is a modern VPN protocol praised for its speed and reliability. Its ability to quickly reconnect after network changes makes it particularly ideal for mobile devices. IKEv2 ensures strong security by leveraging IPsec for both encryption and authentication. However, it may not be as widely supported across all platforms, which can limit its compatibility.
VPN Protocol Comparison
When selecting a VPN protocol, key factors such as speed, security, compatibility, and ease of use should be considered. OpenVPN is a popular choice due to its robust security and flexibility, while L2TP/IPsec and IKEv2 strike a good balance between security and performance. The best protocol for you will ultimately depend on your specific requirements and preferences.
Conclusion
In conclusion, VPN protocols are essential in maintaining the privacy and security of internet users. Whether you’re streaming, handling sensitive data, or just browsing online, selecting the appropriate protocol is key to ensuring your data remains protected. By understanding the distinctions between protocols such as OpenVPN, L2TP/IPsec, and IKEv2, you can make a well-informed choice to enhance the security of your online activities.

